




 Subscribe
Subscribe
 Follow Us!
Follow Us!
 Be Our Fan
Be Our Fan



That words across my mine during web-surfing, while my gmail and iGoogle account still logged in. Moreover I like Chrome to get any information through internet. Does Google really spy on me? If you open History in Chrome, you will be amazed by how well-organize Chrome doing it.

With Google+, the behemoth of Web search may have finally figured out social networking. Demand for Google+ invites is reportedly through the roof, and critics are generally pleased with how the service works..

At last. Angry Birds is now available in the Windows Phone Marketplace—a few hours ahead of schedule and so fresh it hasn’t even been rated yet! Be the first—or just hunker down with your phone and get dem pigs. .
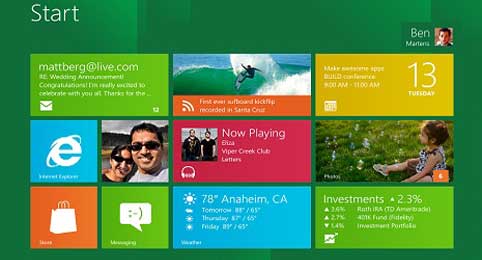
On Tuesday, Microsoft showed off the first tablets running Windows 8, and provided a bunch of new details about the operating system.

Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.




| Reactions: |

| Reactions: |
|
| click on picture to enlarge |
| Reactions: |

| Reactions: |

| Reactions: |
 Under the cover of night, the soldiers snuck out and opened the gates of the city, and later, together with the rest of the army, killed the entire army of Troy.
Under the cover of night, the soldiers snuck out and opened the gates of the city, and later, together with the rest of the army, killed the entire army of Troy.| Reactions: |
 A man pirated $5 million of content in the name of art!
A man pirated $5 million of content in the name of art!| Reactions: |

| Reactions: |

| Reactions: |
Get your own Digital Clock![]()
Enter your email address:
Delivered by FeedBurner



↑ Grab this Headline Animator


↑ Grab this Headline Animator
